SAMS
ServIT Asset Monitoring Systems
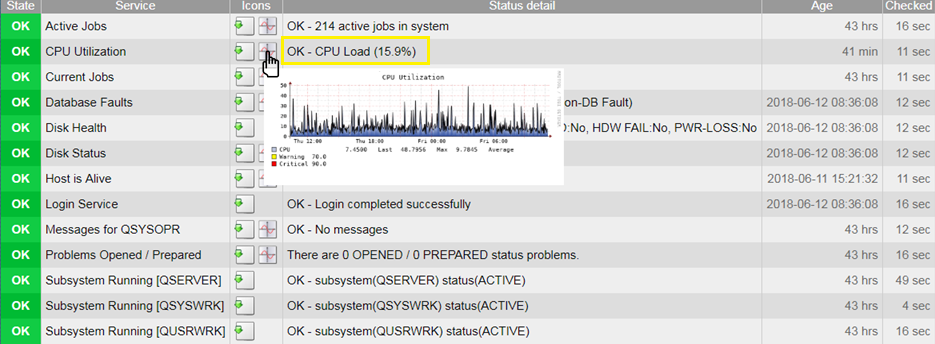
ServIT set out to design a custom tool to address a well-known gap in the ability of our clients to monitor, manage, and report within their AS/400 environment. During our development process, the capabilities of this system continued to grow and evolve. We discovered not only had we succeeded in developing the tool we set out to build, but we now had the ability to monitor everything in the AS/400’s complete dependency stack. That is when the SAMS was born.
The SAMS (ServIT Asset Monitoring System) is a purpose-built micro appliance allowing an in-depth view into your entire AS/400 ecosystem including, all of the systems and services that make it available to your people and your processes.
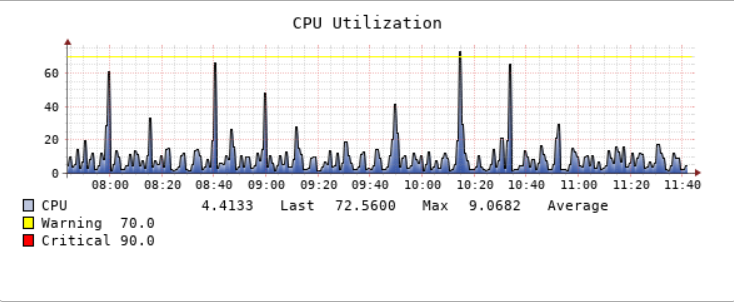
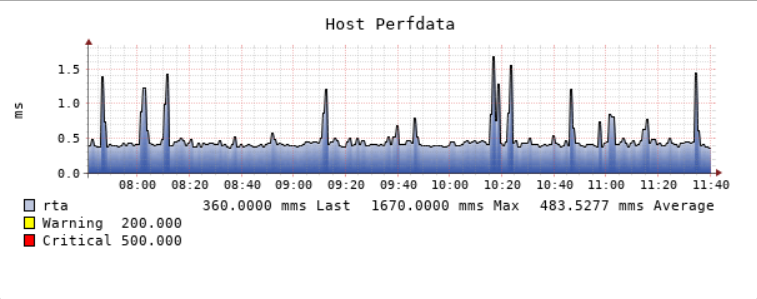
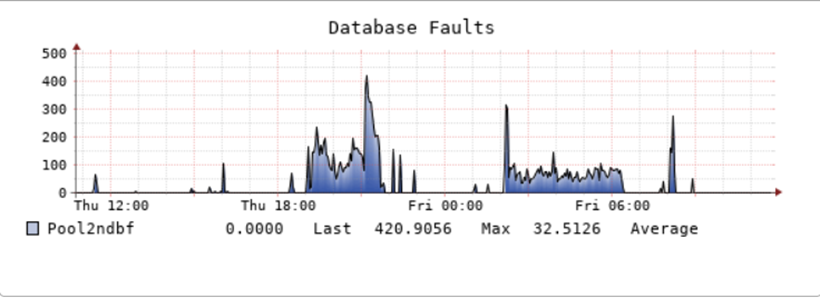
The SAMS is simple. After an initial onboarding that usually takes less than an hour, all you have to do is plug the SAMS into a port on your switch. Within minutes, we will be able to monitor availability from your ISP to your Firewall to the Switch, to the Port, to the Ethernet Connection, to the AS/400 to the Subsystem, and to the Job or Process — as high-level or as granular as is required.
While the form-factor remains small, its capabilities are HUGE.
iSysmon
In addition to our micro appliance-based monitoring, ServIT has also developed the best agent-based AS400 hardware monitoring tool in the industry – iSysmon. Information is useless unless it’s actionable. iSysmon provides a real-time, granular, 360° view into how your AS400 is performing in your environment allowing you to be proactive in your management and fine-tuning of your AS400 instead of spending your time putting out fires.