Operating Systems supported by Carbon Black.
- Windows 7/8/10
- Windows Server 2008/2012/2016
- MacOS
- RHEL/CentOS
- Ubuntu
- SUSE
- Amazon Linux



Not all MSPs are created equal
ServIT seeks to be the highest-value managed service provider on the planet. NO MSP has the knowledge, skills, and experience required to specialize in Cybersecurity / SOC (Security Operations Center) — this is a highly-specialized, mission-critical field that stands on its own.
ServIT has searched the globe to find the best cybersecurity experts in the world to support our valued clients. We found them. And, we are proud to offer the world’s first smart SOC as a Service.
Our SOC as a Service offering is designed, executed, and operated by elite cybersecurity experts with both nation-state and corporate-level expertise. Our team will allow you to grow your business while keeping a secure working environment. As we are enhancing your cybersecurity defense capabilities, we will act as an extension to your security team.
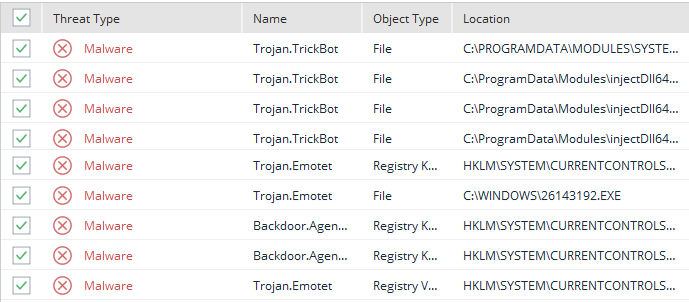
Not all security operations centers are the same
In general, there are four tiers of SOC services each having vital functions. However, as a rule, they all have two common foundations with security monitoring tools to receive contextually relevant information from both inside and outside the network (e.g., persistent outbound data transfers, login/ logoff, firewall activity, etc.). In addition, these systems monitor cloud and on-premise infrastructure services like DNS, email, web, domain controllers, and active directory services.
Tier 1-3 SOCs focus on the tactical activities of managing an SOC either defensively (Tier 1-2), or proactively hunting threats (Tier 3). At this level, the service provider typically oversees all aspects of a proactive – threat hunter – SOC operation. This includes managing incident response programs, escalation processes, and developing the crisis communications plan across the organization. Tier 4 SOCs produce, report, and maintain performance metrics to protect their customer’s executives, brands, and reputations.
Learn how we can be the perfect IT solution for your business.
